Learn how to generate credentials needed by Autobahn to activate OIDC SSO with this guide
Table of content
- OIDC SSO with Okta in Autobahn
- Prerequisites for OIDC with Okta
- Create app integration
- Test the login
1. OIDC SSO with Okta in Autobahn
Okta is an identity management service, built for the cloud, but compatible with many on-premises applications. This guide will help you generate the necessary credentials within your Okta environment to enable Autobahn's SSO.
2. Prerequisites for OIDC with Okta
To configure OIDC SSO using Okta, you need to provide these credentials:
-
Client ID
-
Client Secret
To collect the Client ID and Client secret follow the steps below.
3. Create app integration
1 - Log in to Okta and navigate to the Admin panel.
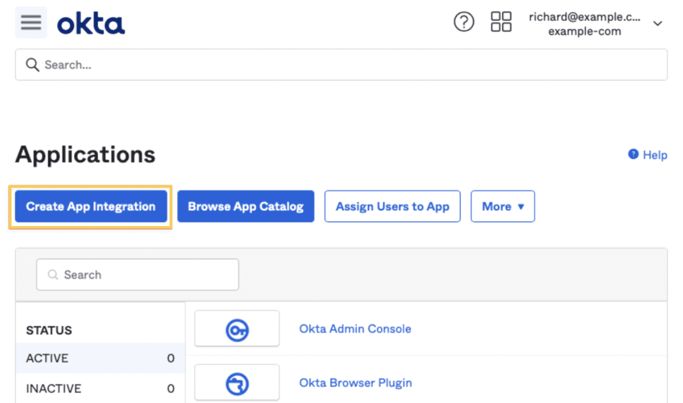
2 - Navigate to Applications -> Applications and click the Create App Integration button.
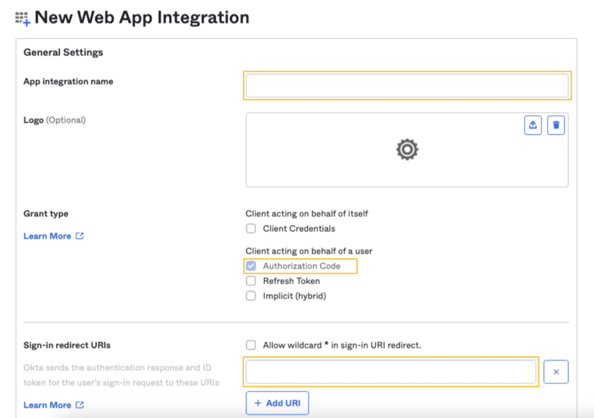
3 - Select OIDC - OpenID Connect and Web Application then click Next.

4 - Enter an App integration name and ensure that the Authorization Code is checked. Then, add this URL on the Sign-in redirect URI field.
https://identity.autobahn-security.com/oauth2/callback
5 - Scroll down. Under the Assignments section, select Skip group assignment for now. Hit Save.

6 - Copy the Client ID and Secret into a text file and send it to the Autobahn team.

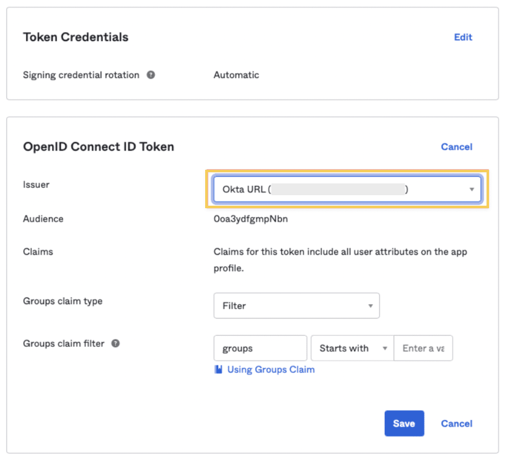
7 - Under Sign On, navigate to OpenID Connect ID Token and change the Issuer to "use the Okta URL". Hit Save and copy this URL into a text file.
8 - Navigate to Directory -> People and click on the username of the user that you would like to authenticate.
9 - Then click Assign Applications and hit the Assign button next to the one you created.
10 - Then click Save and you are done. 🎉
4. Test the login
Once the setup is complete, the Autobahn team will notify you. To verify if the SSO is active, visit the Autobahn login page.
1 - Click the Login with company account button.

2 - Input your company email and you should be successfully logged in.

